Zero-day vulnerabilities are a particular type of error in software applications. This is important because it enables attackers to exploit potentially serious security weaknesses on websites. eCommerce threats that endanger today’s economy.
In this new era of eCommerce business, these types of vulnerabilities have become more and more costly to companies and customers around the world.
While zero-day vulnerabilities are known for being exploited by criminals trying to make a quick buck. Government security agencies have also taken advantage of these security vulnerabilities and used them for surveillance or attacks (Frankenfield, 2019).
As we all know, writing the perfect code is out of the questions. Consequently, to minimize software vulnerabilities companies, have to constantly test and review there software. That is why open-source software has become a great alternative to proprietary software. In the last decade, WordPress one of the open-source alternatives has become the number one platform used to develop all types of websites. The type of websites built with WordPress includes blog, business website, and eCommerce websites as well.
Every year, hundreds of volunteer programmers donate their time to review open-source software to make it safer. Unfortunately, zero-day vulnerabilities can sometimes escape into public consumption. Consequently, creating a potential problem for websites trying to reach the markets and putting in danger all site visitors.
Technical Description of the eCommerce Threats
In the last couple of years, Zero-day vulnerabilities affected some of the most popular web design platforms like WordPress and Drupal. For example, last year a vulnerability found in a WordPress eCommerce plugin call WooCommerce threatened more than 60,000 websites using the vulnerable plugin. The flaw affecting WordPress websites existed within the WooCommerce checkout enabling possible attackers to execute arbitrary file uploads. (Hashim, 2019).
As the name suggests, arbitrary file upload vulnerabilities are a type of vulnerability that occurs in web applications file upload system. An attacker who has gained unauthorized access to such vulnerability can upload a malicious script that can control and execute the desired commands, which could lead to a full compromise of the server.
This type of vulnerability could also allow direct access to the website database. This is accomplished by failing to filter and sanitize the eCommerce store input fields. Consequently, allowing unauthenticated users the power to change database information via a specially crafted and malicious request.
Recent History and the Impact on eCommerce Website
Several cybersecurity firms that specialized in investigating WordPress security plugins and WordPress themes have reported on an increasing number of attacks on WordPress sites.
Last February, Wordfence reported that hackers have been exploiting a zero-day vulnerability in the Duplicator plugin. This is a plugin that allows website administrators to export the website and database content into another server. Exploiting this vulnerability can critically damage an eCommerce store by stealing client data stored it the website database. Besides, the attackers can sell the duplicated website to the eCommerce website competitors (Climpanu, 2020).
Another vulnerability designed to affect eCommerce websites was found in a plugin called Flexible Checkout Fields. This plugin is installed in more than 20,000 WooCommerce websites. Attackers are taking advantage of the unpatched and inject XSS payloads that can be triggered in the dashboard of a logged-in administrator. These XSS payloads permitted unauthorized users to create administrator accounts on vulnerable eCommerce websites.
eCommerce Threats Risk Assessment
A risk assessment needs to be taken into consideration when an organization is building a new online business. There are many things that new to be put into consideration. Choosing the right tool for the job will provide you with the best alternative to minimize the risk of investment.
A risk assessment will help to identify and analyze potential events that may negatively impact the company’s assets. The business and information technology department needs to take the usual security precautions. The big questions are how to maintain a secure platform and what are the risks of using this tool for the job?
Even if your organization does not plan to offer products or services, unauthorized access to the company’s data may prove to be a dangerous threat to the health of the business. Most people who work in Cybersecurity have probably heard the term zero-day attack. In the cyber world, system vulnerability or weakness is something that must be addressed immediately.
To minimize the risks, companies must implement a set of security rules. Many companies have decided to use the WordPress platform as their main tool for business. Maintain up to data patches is the key to maintaining your website away from those critical zero-day vulnerabilities.
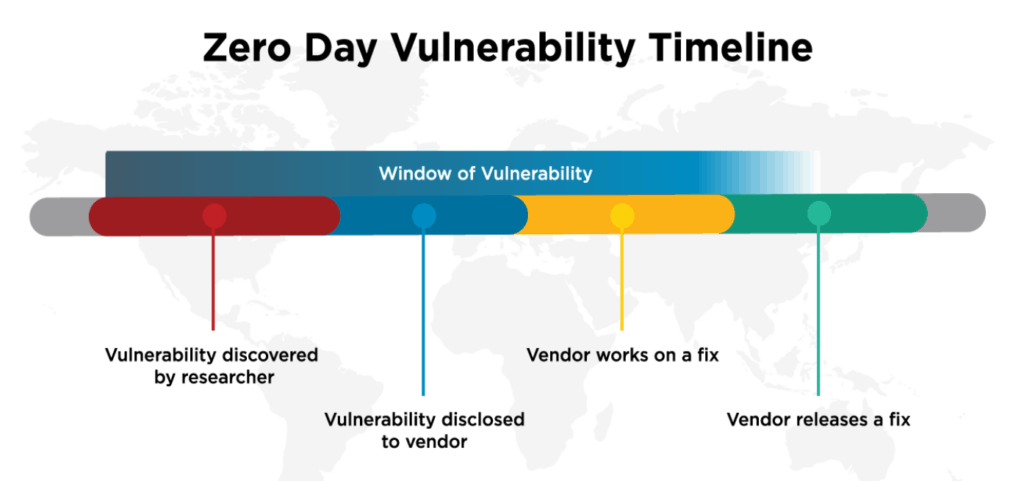
Closing the Zero-day Window of Vulnerability
The Window of Vulnerability for zero-day exploits is the time between when a vulnerability becomes known to the general public and the time when a fix is released by the vendor. Most of the way vulnerabilities are found varies between platforms and communities (WordFence, 2018).
- Vulnerabilities are found by a company researcher or a malicious actor.
- When a vulnerability is exposed the vulnerability stops being a Zero Day and the vendor has had to fix the issue.
- The vendor may or may not publicly acknowledge that it is a valid security problem.
- The company’s programmers work on developing a fix.
- The vendor releases the fix either as a regularly scheduled update or releases an emergency release containing the fix to their customers.
Conclusion
In the world of cybersecurity, Zero-day vulnerabilities are unintended flaws found in software programs or operating systems. Vulnerabilities can be the result of improper computer or security configurations and programming errors. If left unaddressed, vulnerabilities create security holes that cybercriminals can exploit.
Even though it is almost impossible to stop zero-day attacks, updating your software and constantly backing up your system is the key strategy to minimize the effects of an attack.
References
Frankenfield, J. (06/2019). Zero-Day Attack Retrieved from https://www.investopedia.com/terms/z/zero-day-attack.asp
Hashim, A. (04/2019). WordPress WooCommerce Plugin Vulnerability Permit Arbitrary File Add. Retrieved from https://ethhack.com/2019/04/wordpress-woocommerce-plugin-vulnerability-allow-arbitrary-file-upload
Climpanu, C. (03/2020) Hackers are actively exploiting zero-days in several WordPress plugins. Retrieved from https://www.zdnet.com/article/hackers-are-actively-exploiting-zero-days-in-several-wordpress-plugins
WordFence. (06/2018) Understanding Zero-Day Exploits & Disclosures. Retrieved from https://www.wordfence.com/learn/understanding-zero-day-exploits
