Category: Computer Network
-
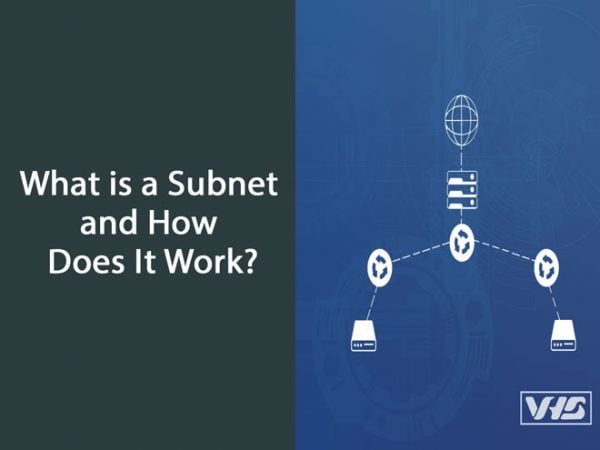
What is a Subnet and How Does It Work?
In this post, I’m going to talk about the concept of network IP address subnets and the benefits of subnetting. Let’s begin by answering the main question of this blog post. What is a subnet? A subnetwork or subnet is a logical subdivision of an IP network. The practice of dividing a network into two…
-

Samba Server: How to Install and Configure on Ubuntu
Let’s start by answering the first questions that came to my mind. Why do I need a Samba in your network? Samba is free and open-source software that enables file sharing across different operating systems over a network. This is an alternative Linux implementation to the Windows SMB protocol. Below are the 4 most common…
-

How To Install Ubuntu Linux
This article will focus on the step-by-step instructions on how to install Ubuntu. First of all, here is an intro to the popular Debian-based Operating system. Ubuntu Linux is one of the most popular free operating systems in the world. Mainly, thanks to the great community behind this project and to Canonical, the company in charge…
-

What are Binary and Hexadecimal Number Systems?
There are three numbering systems that every network engineer needs to know decimal, binary, and hexadecimal. We all know how the decimal system work, so let’s begin with the introduction to the binary system. A basic understanding of the binary system and how to convert to a decimal system is an essential tool for anyone…
-

What are The Well-Known Port Numbers?
A port number is a 16-bit numeric value that oscillates between 0 and 65535. There are three different types of port numbers: well-known ports, registered ports, and dynamic ports. Therefore, making port numbers an essential part of network communication. Consequently, make sure to review these while studying for your next certification (CCNA or CompTIA Network+). First…
-

What is the OSI model?
The Open Systems Interconnection (OSI) or OSI Model was invented as a representation to standardize communication between two computers. This networking model divides the networking process into 7 layers. Above all, these standards serve as a guide that helps vendors and developers create devices that interoperate with each other regardless of the brand. All these 7 layers work collaboratively…
-

What is an IP Address?
An IP address is one of the most important parts of network connectivity. That is to say, that this is the most important tool that computers use to communicate with each other over a network. First of all, the reason you are reading this article is that you need the answer to one important question.…
-

What is Internet Protocol (IP)?
So, what is an internet protocol (IP)? Let me start by providing you with the technical definition of your question. The Internet Protocol or commonly known as “IP” is a set of requirements or instructions for routing packets of data traveling thru a network. These rules direct these packages of data into their correct destination.…
-

Benefits of IT Certifications
Why should you earn an IT certification? What are the benefits of IT certifications? Which certification should I get? These are some of the most common questions about IT certifications. These are the question I will try to answer in this article. First, let’s begin by understanding how to get an IT certification. An IT…
-

What is Linux & all its Distributions?
A Linux distribution or Linux distro is an operating system that consists of a collection of open-source software based on the Linux kernel and a package management system. Above all, each Linux distribution includes the Linux kernel as the foundation of the operating system. Secondly, it includes the GNU shell utilities as the terminal interface. In addition, this distribution also consists of…
-
What is a Virtual Machine?
A virtual machine (VM) is a virtual computer that works like a computer within a computer. This virtual computer system runs on isolated partitions. These VMs has their own operating system with dedicated amounts of CPU, memory, and storage that are borrowed from the physical host computer. Most importantly, the whole system is contained within a computer…
